i. Did your peer’s assessment of the different theories offer new insights to you?
ii. What questions remain in your mind after reading their analyses of these change model? Invite further conversation about these theories.
HBR’s 10 Must Reads on Change Management: The Hard Side of Change Management
The Hard Side of Change Management
by Harold L. Sirkin, Perry Keenan, and Alan Jackson
WHEN FRENCH NOVELIST JEAN-BAPTISTE Alphonse Karr wrote “Plus ça change, plus c’est la même chose,” he could have been penning an epigram about change management. For over three decades, academics, managers, and consultants, realizing that transforming organizations is difficult, have dissected the subject. They’ve sung the praises of leaders who communicate vision and walk the talk in order to make change efforts succeed. They’ve sanctified the importance of changing organizational culture and employees’ attitudes. They’ve teased out the tensions between top-down transformation efforts and participatory approaches to change. And they’ve exhorted companies to launch campaigns that appeal to people’s hearts and minds. Still, studies show that in most organizations, two out of three transformation initiatives fail. The more things change, the more they stay the same.
Managing change is tough, but part of the problem is that there is little agreement on what factors most influence transformation initiatives. Ask five executives to name the one factor critical for the success of these programs, and you’ll probably get five different answers. That’s because each manager looks at an initiative from his or her viewpoint and, based on personal experience, focuses on different success factors. The experts, too, offer different perspectives. A recent search on Amazon.com for books on “change and management” turned up 6,153 titles, each with a distinct take on the topic. Those ideas have a lot to offer, but taken together, they force companies to tackle many priorities simultaneously, which spreads resources and skills thin. Moreover, executives use different approaches in different parts of the organization, which compounds the turmoil that usually accompanies change.
In recent years, many change management gurus have focused on soft issues, such as culture, leadership, and motivation. Such elements are important for success, but managing these aspects alone isn’t sufficient to implement transformation projects. Soft factors don’t directly influence the outcomes of many change programs. For instance, visionary leadership is often vital for transformation projects, but not always. The same can be said about communication with employees. Moreover, it isn’t easy to change attitudes or relationships; they’re deeply ingrained in organizations and people. And although changes in, say, culture or motivation levels can be indirectly gauged through surveys and interviews, it’s tough to get reliable data on soft factors.
What’s missing, we believe, is a focus on the not-so-fashionable aspects of change management: the hard factors. These factors bear three distinct characteristics. First, companies are able to measure them in direct or indirect ways. Second, companies can easily communicate their importance, both within and outside organizations. Third, and perhaps most important, businesses are capable of influencing those elements quickly. Some of the hard factors that affect a transformation initiative are the time necessary to complete it, the number of people required to execute it, and the financial results that intended actions are expected to achieve. Our research shows that change projects fail to get off the ground when companies neglect the hard factors. That doesn’t mean that executives can ignore the soft elements; that would be a grave mistake. However, if companies don’t pay attention to the hard issues first, transformation programs will break down before the soft elements come into play.
Idea in Brief
Two out of every three transformation programs fail. Why? Companies overemphasize the soft side of change: leadership style, corporate culture, employee motivation. Though these elements are critical for success, change projects can’t get off the ground unless companies address harder elements first.
The essential hard elements? Think of them as DICE:
• Duration: time between milestone reviews—the shorter, the better
• Integrity: project teams’ skill
• Commitment: senior executives’ and line managers’ dedication to the program
• Effort: the extra work employees must do to adopt new processes—the less, the better
By assessing each DICE element before you launch a major change initiative, you can identify potential problem areas and make the necessary adjustments (such as reconfiguring a project team’s composition or reallocating resources) to ensure the program’s success. You can also use DICE after launching a project—to make midcourse corrections if the initiative veers off track.
DICE helps companies lay the foundation for successful change. Using the DICE assessment technique, one global beverage company executed a multiproject organization-wide change program that generated hundreds of millions of dollars, breathed new life into its once-stagnant brands, and cracked open new markets.
That’s a lesson we learned when we identified the common denominators of change. In 1992, we started with the contrarian hypothesis that organizations handle transformations in remarkably similar ways. We researched projects in a number of industries and countries to identify those common elements. Our initial 225-company study revealed a consistent correlation between the outcomes (success or failure) of change programs and four hard factors: project duration, particularly the time between project reviews; performance integrity, or the capabilities of project teams; the commitment of both senior executives and the staff whom the change will affect the most; and the additional effort that employees must make to cope with the change. We called these variables the DICE factors because we could load them in favor of projects’ success.
Idea in Practice
Conducting a DICE Assessment
Your project has the greatest chance of success if the following hard elements are in place:
Duration
A long project reviewed frequently stands a far better chance of succeeding than a short project reviewed infrequently. Problems can be identified at the first sign of trouble, allowing for prompt corrective actions. Review complex projects every two weeks; more straightforward initiatives, every six to eight weeks.
Integrity
A change program’s success hinges on a high-integrity, high-quality project team. To identify team candidates with the right portfolio of skills, solicit names from key colleagues, including top performers in functions other than your own. Recruit people who have problem-solving skills, are results oriented, and are methodical but tolerate ambiguity. Look also for organizational savvy, willingness to accept responsibility for decisions, and a disdain for the limelight.
Commitment
If employees don’t see company leaders supporting a change initiative, they won’t change. Visibly endorse the initiative—no amount of public support is too much. When you feel you’re “talking up” a change effort at least three times more than you need to, you’ve hit it right.
Also continually communicate why the change is needed and what it means for employees. Ensure that all messages about the change are consistent and clear. Reach out to managers and employees through one-on-one conversations to win them over.
Effort
If adopting a change burdens employees with too much additional effort, they’ll resist. Calculate how much work employees will have to do beyond their existing responsibilities to implement the change. Ensure that no one’s workload increases more than 10%. If necessary, remove nonessential regular work from employees with key roles in the transformation project. Use temporary workers or outsource some processes to accommodate additional workload.
Using the DICE Framework
Conducting a DICE assessment fosters successful change by sparking valuable senior leadership debate about project strategy It also improves change effectiveness by enabling companies to manage large portfolios of projects.
Example: A manufacturing company planned 40 projects as part of a profitability-improvement program. After conducting a DICE assessment for each project, leaders and project owners identified the five most important projects and asked, “How can we ensure these projects’ success?” They moved people around on teams, reconfigured some projects, and identified initiatives senior managers should pay more attention to—setting up their most crucial projects for resounding success.
We completed our study in 1994, and in the 11 years since then, the Boston Consulting Group has used those four factors to predict the outcomes, and guide the execution, of more than 1,000 change management initiatives worldwide. Not only has the correlation held, but no other factors (or combination of factors) have predicted outcomes as well.
The Four Key FactorsIf you think about it, the different ways in which organizations combine the four factors create a continuum—from projects that are set up to succeed to those that are set up to fail. At one extreme, a short project led by a skilled, motivated, and cohesive team, championed by top management and implemented in a department that is receptive to the change and has to put in very little additional effort, is bound to succeed. At the other extreme, a long, drawn-out project executed by an inexpert, unenthusiastic, and disjointed team, without any top-level sponsors and targeted at a function that dislikes the change and has to do a lot of extra work, will fail. Businesses can easily identify change programs at either end of the spectrum, but most initiatives occupy the middle ground where the likelihood of success or failure is difficult to assess. Executives must study the four DICE factors carefully to figure out if their change programs will fly—or die.
The Four Factors
THESE FACTORS determine the outcome of any transformation initiative.
D. The duration of time until the change program is completed if it has a short life span; if not short, the amount of time between reviews of milestones.
I. The project team’s performance integrity; that is, its ability to complete the initiative on time. That depends on members’ skills and traits relative to the project’s requirements.
C. The commitment to change that top management (C1) and employees affected by the change (C2) display.
E. The effort over and above the usual work that the change initiative demands of employees.
DurationCompanies make the mistake of worrying mostly about the time it will take to implement change programs. They assume that the longer an initiative carries on, the more likely it is to fail—the early impetus will peter out, windows of opportunity will close, objectives will be forgotten, key supporters will leave or lose their enthusiasm, and problems will accumulate. However, contrary to popular perception, our studies show that a long project that is reviewed frequently is more likely to succeed than a short project that isn’t reviewed frequently. Thus, the time between reviews is more critical for success than a project’s life span.
Companies should formally review transformation projects at least bimonthly since, in our experience, the probability that change initiatives will run into trouble rises exponentially when the time between reviews exceeds eight weeks. Whether reviews should be scheduled even more frequently depends on how long executives feel the project can carry on without going off track. Complex projects should be reviewed fortnightly; more familiar or straightforward initiatives can be assessed every six to eight weeks.
Scheduling milestones and assessing their impact are the best way by which executives can review the execution of projects, identify gaps, and spot new risks. The most effective milestones are those that describe major actions or achievements rather than day-to-day activities. They must enable senior executives and project sponsors to confirm that the project has made progress since the last review took place. Good milestones encompass a number of tasks that teams must complete. For example, describing a particular milestone as “Consultations with Stakeholders Completed” is more effective than “Consult Stakeholders” because it represents an achievement and shows that the project has made headway. Moreover, it suggests that several activities were completed—identifying stakeholders, assessing their needs, and talking to them about the project. When a milestone looks as though it won’t be reached on time, the project team must try to understand why, take corrective actions, and learn from the experience to prevent problems from recurring.
Review of such a milestone—what we refer to as a “learning milestone”—isn’t an impromptu assessment of the Monday-morning kind. It should be a formal occasion during which senior-management sponsors and the project team evaluate the latter’s performance on all the dimensions that have a bearing on success and failure. The team must provide a concise report of its progress, and members and sponsors must check if the team is on track to complete, or has finished all the tasks to deliver, the milestone. They should also determine whether achieving the milestone has had the desired effect on the company; discuss the problems the team faced in reaching the milestone; and determine how that accomplishment will affect the next phase of the project. Sponsors and team members must have the power to address weaknesses. When necessary, they should alter processes, agree to push for more or different resources, or suggest a new direction. At these meetings, senior executives must pay special attention to the dynamics within teams, changes in the organization’s perceptions about the initiative, and communications from the top.
IntegrityBy performance integrity, we mean the extent to which companies can rely on teams of managers, supervisors, and staff to execute change projects successfully. In a perfect world, every team would be flawless, but no business has enough great people to ensure that. Besides, senior executives are often reluctant to allow star performers to join change efforts because regular work can suffer. But since the success of change programs depends on the quality of teams, companies must free up the best staff while making sure that day-to-day operations don’t falter. In companies that have succeeded in implementing change programs, we find that employees go the extra mile to ensure their day-to-day work gets done.
Since project teams handle a wide range of activities, resources, pressures, external stimuli, and unforeseen obstacles, they must be cohesive and well led. It’s not enough for senior executives to ask people at the watercooler if a project team is doing well; they must clarify members’ roles, commitments, and accountability. They must choose the team leader and, most important, work out the team’s composition.
Smart executive sponsors, we find, are very inclusive when picking teams. They identify talent by soliciting names from key colleagues, including human resource managers; by circulating criteria they have drawn up; and by looking for top performers in all functions. While they accept volunteers, they take care not to choose only supporters of the change initiative. Senior executives personally interview people so that they can construct the right portfolio of skills, knowledge, and social networks. They also decide if potential team members should commit all their time to the project; if not, they must ask them to allocate specific days or times of the day to the initiative. Top management makes public the parameters on which it will judge the team’s performance and how that evaluation fits into the company’s regular appraisal process. Once the project gets under way, sponsors must measure the cohesion of teams by administering confidential surveys to solicit members’ opinions.
Executives often make the mistake of assuming that because someone is a good, well-liked manager, he or she will also make a decent team leader. That sounds reasonable, but effective managers of the status quo aren’t necessarily good at changing organizations. Usually, good team leaders have problem-solving skills, are results oriented, are methodical in their approach but tolerate ambiguity, are organizationally savvy, are willing to accept responsibility for decisions, and while being highly motivated, don’t crave the limelight. A CEO who successfully led two major transformation projects in the past ten years used these six criteria to quiz senior executives about the caliber of nominees for project teams. The top management team rejected one in three candidates, on average, before finalizing the teams.
CommitmentCompanies must boost the commitment of two different groups of people if they want change projects to take root: They must get visible backing from the most influential executives (what we call C1), who are not necessarily those with the top titles. And they must take into account the enthusiasm—or often, lack thereof—of the people who must deal with the new systems, processes, or ways of working (C2).
Top-level commitment is vital to engendering commitment from those at the coal face. If employees don’t see that the company’s leadership is backing a project, they’re unlikely to change. No amount of top-level support is too much. In 1999, when we were working with the CEO of a consumer products company, he told us that he was doing much more than necessary to display his support for a nettlesome project. When we talked to line managers, they said that the CEO had extended very little backing for the project. They felt that if he wanted the project to succeed, he would have to support it more visibly! A rule of thumb: When you feel that you are talking up a change initiative at least three times more than you need to, your managers will feel that you are backing the transformation.
Sometimes, senior executives are reluctant to back initiatives. That’s understandable; they’re often bringing about changes that may negatively affect employees’ jobs and lives. However, if senior executives do not communicate the need for change, and what it means for employees, they endanger their projects’ success. In one financial services firm, top management’s commitment to a program that would improve cycle times, reduce errors, and slash costs was low because it entailed layoffs. Senior executives found it gut-wrenching to talk about layoffs in an organization that had prided itself on being a place where good people could find lifetime employment. However, the CEO realized that he needed to tackle the thorny issues around the layoffs to get the project implemented on schedule. He tapped a senior company veteran to organize a series of speeches and meetings in order to provide consistent explanations for the layoffs, the timing, the consequences for job security, and so on. He also appointed a well-respected general manager to lead the change program. Those actions reassured employees that the organization would tackle the layoffs in a professional and humane fashion.
Companies often underestimate the role that managers and staff play in transformation efforts. By communicating with them too late or inconsistently, senior executives end up alienating the people who are most affected by the changes. It’s surprising how often something senior executives believe is a good thing is seen by staff as a bad thing, or a message that senior executives think is perfectly clear is misunderstood. That usually happens when senior executives articulate subtly different versions of critical messages. For instance, in one company that applied the DICE framework, scores for a project showed a low degree of staff commitment. It turned out that these employees had become confused, even distrustful, because one senior manager had said, “Layoffs will not occur,” while another had said, “They are not expected to occur.”
Organizations also underestimate their ability to build staff support. A simple effort to reach out to employees can turn them into champions of new ideas. For example, in the 1990s, a major American energy producer was unable to get the support of mid-level managers, supervisors, and workers for a productivity improvement program. After trying several times, the company’s senior executives decided to hold a series of one-on-one conversations with mid-level managers in a last-ditch effort to win them over. The conversations focused on the program’s objectives, its impact on employees, and why the organization might not be able to survive without the changes. Partly because of the straight talk, the initiative gained some momentum. This allowed a project team to demonstrate a series of quick wins, which gave the initiative a new lease on life.
EffortWhen companies launch transformation efforts, they frequently don’t realize, or know how to deal with the fact, that employees are already busy with their day-to-day responsibilities. According to staffing tables, people in many businesses work 80-plus-hour weeks. If, on top of existing responsibilities, line managers and staff have to deal with changes to their work or to the systems they use, they will resist.
Project teams must calculate how much work employees will have to do beyond their existing responsibilities to change over to new processes. Ideally, no one’s workload should increase more than 10%. Go beyond that, and the initiative will probably run into trouble. Resources will become overstretched and compromise either the change program or normal operations. Employee morale will fall, and conflict may arise between teams and line staff. To minimize the dangers, project managers should use a simple metric like the percentage increase in effort the employees who must cope with the new ways feel they must contribute. They should also check if the additional effort they have demanded comes on top of heavy workloads and if employees are likely to resist the project because it will demand more of their scarce time.
Companies must decide whether to take away some of the regular work of employees who will play key roles in the transformation project. Companies can start by ridding these employees of discretionary or nonessential responsibilities. In addition, firms should review all the other projects in the operating plan and assess which ones are critical for the change effort. At one company, the project steering committee delayed or restructured 120 out of 250 subprojects so that some line managers could focus on top-priority projects. Another way to relieve pressure is for the company to bring in temporary workers, like retired managers, to carry out routine activities or to outsource current processes until the changeover is complete. Handing off routine work or delaying projects is costly and time-consuming, so companies need to think through such issues before kicking off transformation efforts.
Calculating DICE Scores
COMPANIES CAN DETERMINE if their change programs will succeed by asking executives to calculate scores for each of the four factors of the DICE framework—duration, integrity, commitment, and effort. They must grade each factor on a scale from 1 to 4 (using fractions, if necessary); the lower the score, the better. Thus, a score of 1 suggests that the factor is highly likely to contribute to the program’s success, and a score of 4 means that it is highly unlikely to contribute to success. We find that the following questions and scoring guidelines allow executives to rate transformation initiatives effectively:
Duration [D]
Ask: Do formal project reviews occur regularly? If the project will take more than two months to complete, what is the average time between reviews?
Score: If the time between project reviews is less than two months, you should give the project 1 point. If the time is between two and four months, you should award the project 2 points; between four and eight months, 3 points; and if reviews are more than eight months apart, give the project 4 points.
Integrity of Performance [I]
Ask: Is the team leader capable? How strong are team members’ skills and motivations? Do they have sufficient time to spend on the change initiative?
Score: If the project team is led by a highly capable leader who is respected by peers, if the members have the skills and motivation to complete the project in the stipulated time frame, and if the company has assigned at least 50% of the team members’ time to the project, you can give the project 1 point. If the team is lacking on all those dimensions, you should award the project 4 points. If the team’s capabilities are somewhere in between, assign the project 2 or 3 points.
Senior Management Commitment [C1]
Ask: Do senior executives regularly communicate the reason for the change and the importance of its success? Is the message convincing? Is the message consistent, both across the top management team and over time? Has top management devoted enough resources to the change program?
Score: If senior management has, through actions and words, clearly communicated the need for change, you must give the project 1 point. If senior executives appear to be neutral, it gets 2 or 3 points. If managers perceive senior executives to be reluctant to support the change, award the project 4 points.
Local-Level Commitment [C2]
Ask: Do the employees most affected by the change understand the reason for it and believe it’s worthwhile? Are they enthusiastic and supportive or worried and obstructive?
Score: If employees are eager to take on the change initiative, you can give the project 1 point, and if they are just willing, 2 points. If they’re reluctant or strongly reluctant, you should award the project 3 or 4 points.
Effort [E]
Ask: What is the percentage of increased effort that employees must make to implement the change effort? Does the incremental effort come on top of a heavy workload? Have people strongly resisted the increased demands on them?
Score: If the project requires less than 10% extra work by employees, you can give it 1 point. If it’s 10% to 20% extra, it should get 2 points. If it’s 20% to 40%, it must be 3 points. And if it’s more than 40% additional work, you should give the project 4 points.
Executives can combine the four elements into a project score. When we conducted a regression analysis of our database of change efforts, we found that the combination that correlates most closely with actual outcomes doubles the weight given to team performance (I) and senior management commitment (C1). That translates into the following formula:
DICE Score = D + (2 x I) + (2 x C1) + C2 + E
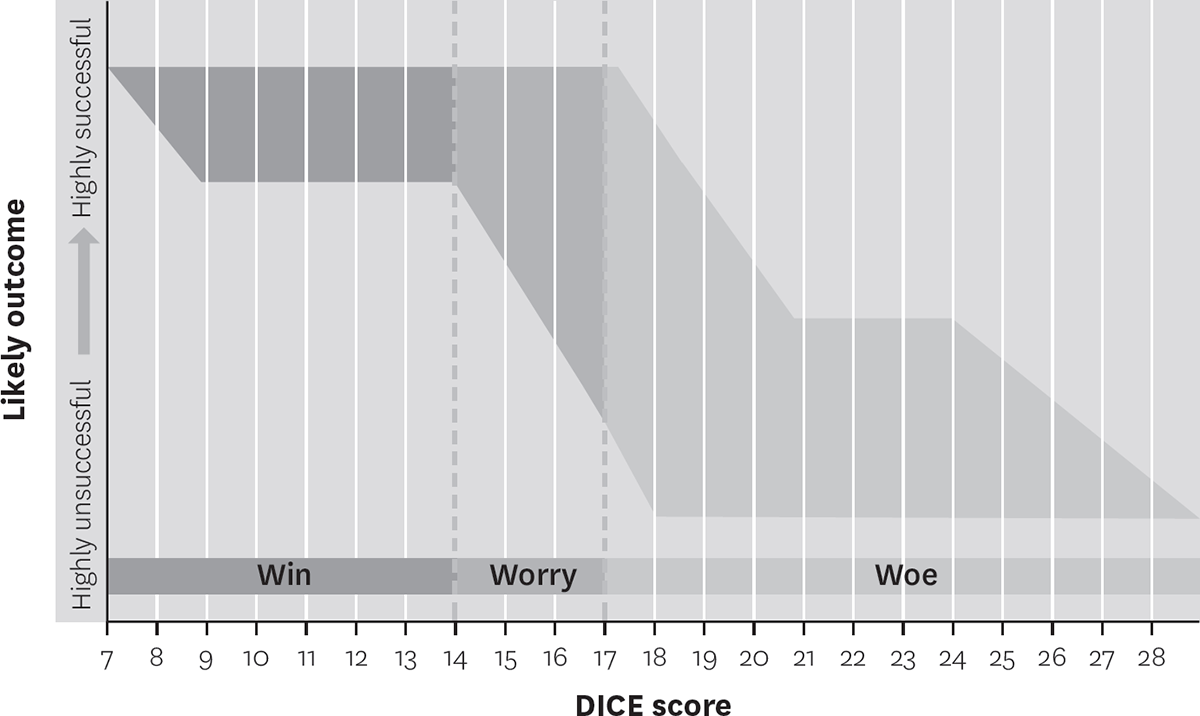
In the 1-to-4 scoring system, the formula generates overall scores that range from 7 to 28. Companies can compare a project’s score with those of past projects and their outcomes to assess if the project is slated for success or failure. Our data show a clear distribution of scores:
Scores between 7 and 14: The project is very likely to succeed. We call this the Win Zone.
Scores higher than 14 but lower than 17: Risks to the project’s success are rising, particularly as the score approaches 17. This is the Worry Zone.
Scores over 17: The project is extremely risky. If a project scores over 17 and under 19 points, the risks to success are very high. Beyond 19, the project is unlikely to succeed. That’s why we call this the Woe Zone.
We have changed the boundaries of the zones over time. For instance, the Worry Zone was between 14 and 21 points at first, and the Woe Zone from 21 to 28 points. But we found that companies prefer to be alerted to trouble as soon as outcomes become unpredictable (17 to 20 points). We therefore compressed the Worry Zone and expanded the Woe Zone.
Creating the FrameworkAs we came to understand the four factors better, we created a framework that would help executives evaluate their transformation initiatives and shine a spotlight on interventions that would improve their chances of success. We developed a scoring system based on the variables that affect each factor. Executives can assign scores to the DICE factors and combine them to arrive at a project score. (See the sidebar “Calculating DICE Scores.”)
Although the assessments are subjective, the system gives companies an objective framework for making those decisions. Moreover, the scoring mechanism ensures that executives are evaluating projects and making trade-offs more consistently across projects.
A company can compare its DICE score on the day it kicks off a project with the scores of previous projects, as well as their outcomes, to check if the initiative has been set up for success. When we calculated the scores of the 225 change projects in our database and compared them with the outcomes, the analysis was compelling. Projects clearly fell into three categories, or zones: Win, which means that any project with a score in that range is statistically likely to succeed; worry, which suggests that the project’s outcome is hard to predict; and woe, which implies that the project is totally unpredictable or fated for mediocrity or failure. (See the figure “DICE scores predict project outcomes.”)
Companies can track how change projects are faring by calculating scores over time or before and after they have made changes to a project’s structure. The four factors offer a litmus test that executives can use to assess the probability of success for a given project or set of projects. Consider the case of a large Australian bank that in 1994 wanted to restructure its back-office operations. Senior executives agreed on the rationale for the change but differed on whether the bank could achieve its objectives, since the transformation required major changes in processes and organizational structures. Bringing the team and the senior executives together long enough to sort out their differences proved impossible; people were just too busy. That’s when the project team decided to analyze the initiative using the DICE framework.
DICE scores predict project outcomes
When we plotted the DICE scores of 225 change management initiatives on the horizontal axis, and the outcomes of those projects on the vertical axis, we found three sets of correlations. Projects with DICE scores between 7 and 14 were usually successful; those with scores over 14 and under 17 were unpredictable; and projects with scores over 17 were usually unsuccessful. We named the three zones Win, Worry, and Woe, respectively. (Each number plotted on the graph represents the number of projects, out of the 225 projects, having a particular DICE score.)
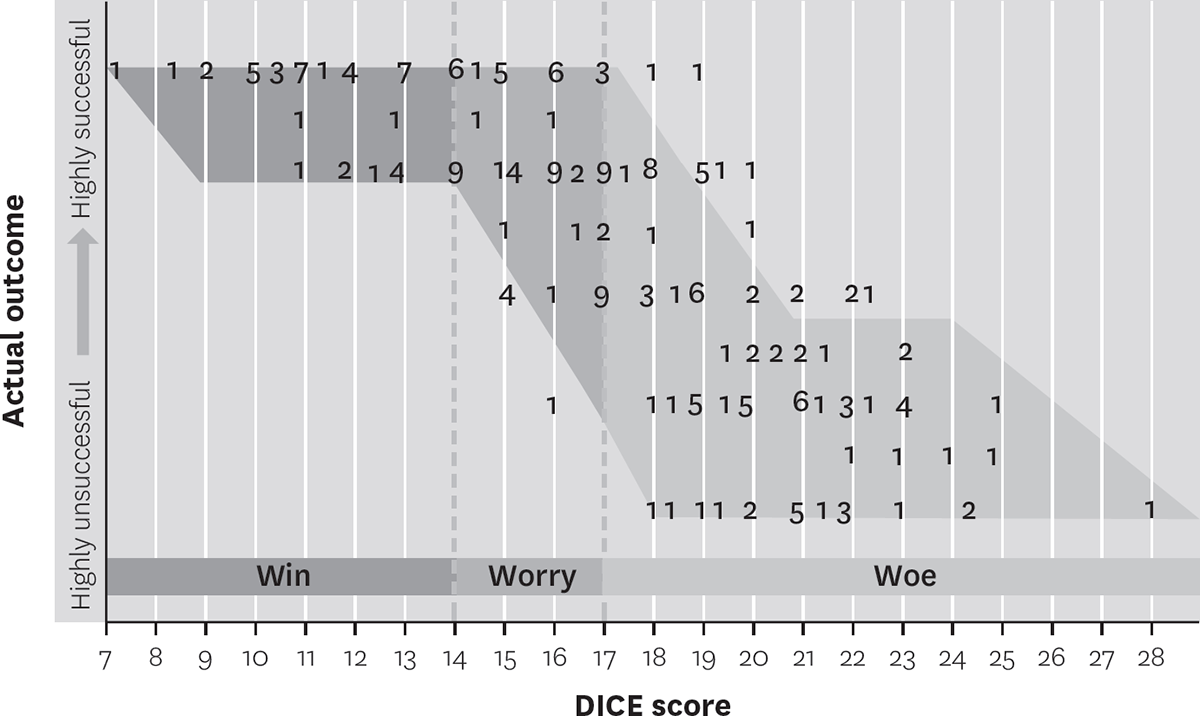
Doing so condensed what could have been a free-flowing two-day debate into a sharp two-hour discussion. The focus on just four elements generated a clear picture of the project’s strengths and weaknesses. For instance, managers learned that the restructuring would take eight months to implement but that it had poorly defined milestones and reviews. Although the project team was capable and senior management showed reasonable commitment to the effort, there was room for improvement in both areas. The back-office workforce was hostile to the proposed changes since more than 20% of these people would lose their jobs. Managers and employees agreed that the back-office staff would need to muster 10% to 20% more effort on top of its existing commitments during the implementation. On the DICE scale, the project was deep in the Woe Zone.
However, the assessment also led managers to take steps to increase the possibility of success before they started the project. The bank decided to split the project time line into two—one short-term and one long-term. Doing so allowed the bank to schedule review points more frequently and to maximize team members’ ability to learn from experience before the transformation grew in complexity. To improve staff commitment, the bank decided to devote more time to explaining why the change was necessary and how the institution would support the staff during the implementation. The bank also took a closer look at the people who would be involved in the project and changed some of the team leaders when it realized that they lacked the necessary skills. Finally, senior managers made a concerted effort to show their backing for the initiative by holding a traveling road show to explain the project to people at all levels of the organization. Taken together, the bank’s actions and plans shifted the project into the Win Zone. Fourteen months later, the bank completed the project—on time and below budget.
Applying the DICE FrameworkThe simplicity of the DICE framework often proves to be its biggest problem; executives seem to desire more complex answers. By overlooking the obvious, however, they often end up making compromises that don’t work. Smart companies try to ensure that they don’t fall into that trap by using the DICE framework in one of three ways.
Track ProjectsSome companies train managers in how to use the DICE framework before they start transformation programs. Executives use spreadsheet-based versions of the tool to calculate the DICE scores of the various components of the program and to compare them with past scores. Over time, every score must be balanced against the trajectory of scores and, as we shall see next, the portfolio of scores.
Senior executives often use DICE assessments as early warning indicators that transformation initiatives are in trouble. That’s how Amgen, the $10.6 billion biotechnology company, used the DICE framework. In 2001, the company realigned its operations around some key processes, broadened its offerings, relaunched some mature products, allied with some firms and acquired others, and launched several innovations. To avoid implementation problems, Amgen’s top management team used the DICE framework to gauge how effectively it had allocated people, senior management time, and other resources. As soon as projects reported troubling scores, designated executives paid attention to them. They reviewed the projects more often, reconfigured the teams, and allocated more resources to them. In one area of the change project, Amgen used DICE to track 300 initiatives and reconfigured 200 of them.
Both big and small organizations can put the tool to good use. Take the case of a hospital that kicked off six change projects in the late 1990s. Each initiative involved a lot of investment, had significant clinical implications, or both. The hospital’s general manager felt that some projects were going well but was concerned about others. He wasn’t able to attribute his concerns to anything other than a bad feeling. However, when the general manager used the DICE framework, he was able to confirm his suspicions. After a 45-minute discussion with project managers and other key people, he established that three projects were in the Win Zone but two were in the Woe Zone and one was in the Worry Zone.
The strongest projects, the general manager found, consumed more than their fair share of resources. Senior hospital staff sensed that those projects would succeed and spent more time promoting them, attending meetings about them, and making sure they had sufficient resources. By contrast, no one enjoyed attending meetings on projects that were performing poorly. So the general manager stopped attending meetings for the projects that were on track; he attended only sessions that related to the three underperforming ones. He pulled some managers from the projects that were progressing smoothly and moved them to the riskier efforts. He added more milestones to the struggling enterprises, delayed their completion, and pushed hard for improvement. Those steps helped ensure that all six projects met their objectives.
Manage portfolios of projectsWhen companies launch large transformation programs, they kick off many projects to attain their objectives. But if executives don’t manage the portfolio properly, those tasks end up competing for attention and resources. For instance, senior executives may choose the best employees for projects they have sponsored or lavish attention on pet projects rather than on those that need attention. By deploying our framework before they start transformation initiatives, companies can identify problem projects in portfolios, focus execution expertise and senior management attention where it is most needed, and defuse political issues.
Take, for example, the case of an Australasian manufacturing company that had planned a set of 40 projects as part of a program to improve profitability. Since some had greater financial implications than others, the company’s general manager called for a meeting with all the project owners and senior managers. The group went through each project, debating its DICE score and identifying the problem areas. After listing all the scores and issues, the general manager walked to a whiteboard and circled the five most important projects. “I’m prepared to accept that some projects will start off in the Worry Zone, though I won’t accept anything outside the middle of this zone for more than a few weeks. For the top five, we’re not going to start until these are well within the Win Zone. What do we have to do to achieve that?” he asked.
The group began thinking and acting right away. It moved people around on teams, reconfigured some projects, and identified those that senior managers should pay more attention to—all of which helped raise DICE scores before implementation began. The most important projects were set up for resounding success while most of the remaining ones managed to get into the Win Zone. The group left some projects in the Worry Zone, but it agreed to track them closely to ensure that their scores improved. In our experience, that’s the right thing to do. When companies are trying to overhaul themselves, they shouldn’t have all their projects in the Win Zone; if they do, they are not ambitious enough. Transformations should entail fundamental changes that stretch an organization.
Force conversationWhen different executives calculate DICE scores for the same project, the results can vary widely. The difference in scores is particularly important in terms of the dialogue it triggers. It provokes participants and engages them in debate over questions like “Why do we see the project in these different ways?” and “What can we agree to do to ensure that the project will succeed?” That’s critical, because even people within the same organization lack a common framework for discussing problems with change initiatives. Prejudices, differences in perspectives, and a reluctance or inability to speak up can block effective debates. By using the DICE framework, companies can create a common language and force the right discussions.
Sometimes, companies hold workshops to review floundering projects. At those two- to four-hour sessions, groups of eight to 15 senior and middle managers, along with the project team and the project sponsors, hold a candid dialogue. The debate usually moves beyond the project’s scores to the underlying causes of problems and possible remedies. The workshops bring diverse opinions to light, which often can be combined into innovative solutions. Consider, for example, the manner in which DICE workshops helped a telecommunications service provider that had planned a major transformation effort. Consisting of five strategic initiatives and 50 subprojects that needed to be up and running quickly, the program confronted some serious obstacles. The projects’ goals, time lines, and revenue objectives were unclear. There were delays in approving business cases, a dearth of rigor and focus in planning and identifying milestones, and a shortage of resources. There were leadership issues, too. For example, executive-level shortcomings had resulted in poor coordination of projects and a misjudgment of risks.
To put the transformation program on track, the telecom company incorporated DICE into project managers’ tool kits. The Project Management Office arranged a series of workshops to analyze issues and decide future steps. One workshop, for example, was devoted to three new product development projects, two of which had landed in the Woe Zone and one in the Worry Zone. Participants traced the problems to tension between managers and technology experts, underfunding, lack of manpower, and poor definition of the projects’ scopes. They eventually agreed on three remedial actions: holding a conflict-resolution meeting between the directors in charge of technology and those responsible for the core business; making sure senior leadership paid immediate attention to the resource issues; and bringing together the project team and the line-of-business head to formalize project objectives. With the project sponsor committed to those actions, the three projects had improved their DICE scores and thus their chances of success at the time this article went to press.
Conversations about DICE scores are particularly useful for large-scale transformations that cut across business units, functions, and locations. In such change efforts, it is critical to find the right balance between centralized oversight, which ensures that everyone in the organization takes the effort seriously and understands the goals, and the autonomy that various initiatives need. Teams must have the flexibility and incentive to produce customized solutions for their markets, functions, and competitive environments. The balance is difficult to achieve without an explicit consideration of the DICE variables.
Take the case of a leading global beverage company that needed to increase operational efficiency and focus on the most promising brands and markets. The company also sought to make key processes such as consumer demand development and customer fulfillment more innovative. The CEO’s goals were ambitious and required investing significant resources across the company. Top management faced enormous challenges in structuring the effort and in spawning projects that focused on the right issues. Executives knew that this was a multiyear effort, yet without tight schedules and oversight of individual projects, there was a risk that projects would take far too long to be completed and the results would taper off.
To mitigate the risks, senior managers decided to analyze each project at several levels of the organization. Using the DICE framework, they reviewed each effort every month until they felt confident that it was on track. After that, reviews occurred when projects met major milestones. No more than two months elapsed between reviews, even in the later stages of the program. The time between reviews at the project-team level was even shorter: Team leaders reviewed progress biweekly throughout the transformation. Some of the best people joined the effort full time. The human resources department took an active role in recruiting team members, thereby creating a virtuous cycle in which the best people began to seek involvement in various initiatives. During the course of the transformation, the company promoted several team members to line- and functional leadership positions because of their performance.
The company’s change program resulted in hundreds of millions of dollars of value creation. Its once-stagnant brands began to grow, it cracked open new markets such as China, and sales and promotion activities were aligned with the fastest-growing channels. There were many moments during the process when inertia in the organization threatened to derail the change efforts. However, senior management’s belief in focusing on the four key variables helped move the company to a higher trajectory of performance.
_____________________
By providing a common language for change, the DICE framework allows companies to tap into the insight and experience of their employees. A great deal has been said about middle managers who want to block change. We find that most middle managers are prepared to support change efforts even if doing so involves additional work and uncertainty and puts their jobs at risk. However, they resist change because they don’t have sufficient input in shaping those initiatives. Too often, they lack the tools, the language, and the forums in which to express legitimate concerns about the design and implementation of change projects. That’s where a standard, quantitative, and simple framework comes in. By enabling frank conversations at all levels within organizations, the DICE framework helps people do the right thing by change.
The Heart of Change: Step 6. Create Short-Term WinsStep 6
Create Short-Term Wins
In successful change efforts, empowered people create short-term wins—victories that nourish faith in the change effort, emotionally reward the hard workers, keep the critics at bay, and build momentum. Without sufficient wins that are visible, timely, unambiguous, and meaningful to others, change efforts inevitably run into serious problems.
The Nature and Function of Short-Term Wins
George has a laser-like focus on a potentially lucrative e-business concept. He leads a team that has dozens of people empowered to pursue various projects, and most of those people are doing so with enthusiasm. From his vantage point, the whole process is incredibly exciting, sometimes scary, and never boring. Twelve months into the effort, he is convinced all is on track, that they have made extraordinary progress under the circumstances. Others who are less enthusiastic begin to raise more and more questions about the initiative. “Yes, this is important, but why are you doing such and such?” “Yes, this is interesting, but isn’t it interfering too much with our current business?” “Yes, but didn’t we try that two years ago and fail?”
Dealing with these questions is distracting, takes time and energy, and ultimately becomes maddening. Every time he thinks he has presented an argument that puts an issue to rest, someone revives it, often with more energy, not less. “Yes, but now I’m really worried about. . . .” He articulates the vision again and again but finds that some people only want to have what seem like metaphysical conversations. He sees these people increasingly as cave dwellers, as creatures who will sooner or later kill the organization, leaving it in the dust. He isolates his staff, putting others in the role of attackers, a role that they increasingly accept. Eventually, key supporters withdraw, and the whole effort is overrun with what seem like infidels. An important and promising set of ideas dies an undistinguished death.
Cary has the same one-year budget and a different, equally powerful, e-business idea. Twelve months into the effort, her group is seemingly behind George’s team. They have fewer projects exploring fewer ideas. They are not as able to fill a report or a meeting with interesting words. But Cary’s people have an up-and-running Web site, a site that is fully developed for one small and carefully targeted customer segment. This small subprototype begins receiving daily customer feedback that looks promising by any standard. Excitement within her group and support from others grow. As George sinks into the mud, Cary begins to soar. George can’t believe her good luck and wonders if her short-term outlook is one more sign that his company is in trouble.
George is a smart and dedicated man. But he doesn’t get it.
In successful change efforts, an empowered group of people are very selective in how they spend their time. They focus first on tasks where they can quickly achieve unambiguous, visible, and meaningful achievements. These short-term wins are essential, serving four important purposes:
1. Wins provide feedback to change leaders about the validity of their visions and strategies.
2. Wins give those working hard to achieve a vision a pat on the back, an emotional uplift.
3. Wins build faith in the effort, attracting those who are not yet actively helping.
4. Wins take power away from cynics.
Without these achievements, large-scale change rarely happens, and the infidels do seem to take over, regardless of how brilliant the vision and how needed the changes. But with these accomplishments, you find the opposite: a growing sense of optimism, of energy, and of belief in change.
Focus Is Essential
Because of the very nature of large-scale change, much must be done to achieve the vision. In sizable organizations, a change effort might ultimately require hundreds of projects. When people feel urgency and are empowered to act, they can easily charge ahead on all fronts. With scattered attention, you might find the first unambiguous wins in two years. Two years is too late.
The List on the Bulletin Boards
From Ross Kao
We have learned that when an organization has a great many things to do to correct its course, those leading the change are tempted to put 150 balls in the air all at one time. There is so much to do, you certainly can find 150 balls to put into play. Everyone can come up with a long list of things. But with so much going on at once, you run the danger of getting nothing finished very fast. This creates problems. It leads to frustration. People wonder where you’re leading them—and whether or not you’re taking the right approach.
To avoid that, we created something called “the Big Four.” We knew what our priorities were. We could have listed the top twenty, but we didn’t. Instead, we went public with just four goals. In essence, we said to the entire organization, “These are the top four things that we’re working on. And until we get one substantially completed, we’re not adding number five.”
We literally published: “Here are the top four.” At every work site we located large bulletin boards that everyone frequented and posted these top four items. In a factory, the board was in the canteen. It quickly became a device for saying, “Look! We’re going to go do something. We’re going to get it done. And guess what? Everybody look! It’s done. And look, we just added another one to the list. And oh, by the way, this one is going to be done in another two weeks.” The next thing you know, people are saying, “You know what? Things are happening. Things are getting done.”
I remember I was out in the factory and I happened to be standing beside the Big Four list. This guy from the line came by and looked at the list with me. After about half a minute he turns to me and he says, “We’re really knocking ‘em down.” People knew it. They felt the energy.
Now, granted, there were some people running around the organization saying, “You mean what I’ve been doing isn’t important?” “No,” we’d say, “that isn’t what we mean. We’re just telling you that that’s not what we’re working on right now. You need to know that what we’re going to do is get something done with lightning speed. We’re going to get it completed, and we’re going to make sure we’ve got enough energy and collective participation to get this thing implemented before we move on to the next item.”
For an organization that had been treading water, creating and communicating our quick wins really helped us begin to gather momentum.
Four instead of 150 means focus. Focus means more is achieved quickly. Quick achievements provide so much: a feeling of accomplishment, a sense of optimism. With this, behavior changes. Those who have worked so hard to create the wins are reenergized. Those who have been pessimistically or skeptically sitting on the sidelines begin to help. Cynics make less disruptive noise. So momentum grows.
Bulletin boards are misused all the time. Put them off to the side where people do not congregate. Clutter the boards with fifty pieces of paper. Put up propaganda (“We’re all committed to the vision!”). Make vague statements (“We’re making progress”). Not in this story.
The Power of Visible, Unambiguous, and Meaningful Wins
Not all wins are equal. In general, the more visible victories are, the more they help the change process. What you don’t know about is not a win—hence, the potential usefulness of a cafeteria bulletin board. The more unambiguous the wins are, the more they help the change process. With less ambiguity, fewer people will argue about whether a success is a success—so power is taken from the cynics. The more the wins speak to employee issues, concerns, and values, the more they help the process. Valued achievements connect to people at a deeper level—and a deeper level can change behavior that is generally very difficult to change.
Creating the New Navy
From Rear Admiral John Totushek
The U.S. Navy has relied upon its Naval Reserve since 1915. The reserve force has consisted of civilians, many of whom are former military members. They train on weekends and work with the active force two weeks each year. They are there to serve in times of war or national emergency.
Historically, the two forces have been managed separately. Now, due to a number of events that began with the collapse of the Soviet Union, our views on our organizations are changing. The active Navy can no longer afford as many full-time regular personnel, which means that they need to rely more and more upon our reserve force. We cannot afford unnecessary duplication of resources. As a result, we have developed a new vision for the Navy and the Naval Reserve—and are creating a new structure in which we are pulling the management of two large organizations closer together. It is both a management challenge and a cultural challenge.
For many years, certainly up until Operation Desert Storm in 1991, reservists were silently acknowledged by some in the active Navy as “just reservists.” They were to be called upon to replenish the active force when it needed more manpower. The active duty forces saw themselves as the ones doing the “real work” of keeping ships and aircraft ready for combat and carrying out operational missions. The reservists were considered “only” a force in waiting. In many commands, active forces would provide work for reservists, but would keep a close, even wary, eye on their “part-time” brethren. In some commands, attitudes developed about not trusting reserve force members with real authority or real responsibility. Yet, with the past decade’s shrinking active force, more responsibility inevitably and necessarily shifted to the reserves, and to the surprise of some of the old guard, the reserves succeeded beyond all expectations. Roles were changing, yet even as we entered the post–Cold War world, old attitudes persisted in the active Navy. These attitudes made it more difficult to pull the two organizations into one Navy.
As we have been trying to change those perceptions, we have been working hard to create successes that would show both the active and reserve forces how interdependence with one another can benefit both—and meld us into one force. We began by discussing goals that were attainable and desirable.
I remember a commander during one of those sessions suggesting that we develop a new curriculum for Officer Candidate School that would focus on educating the active force about the reserve force, and vice versa. The curriculum would focus on our being One Navy. We thought it would be fairly easy to change the curriculum and get our message into the hands of our new officers. If we achieved this, we would achieve something with a long-term, far-reaching impact. We all agreed that getting such a curriculum in place would be a great “win” and would certainly help reinforce our vision in each succeeding generation of sailors. Then someone said, “Yes, but if I am already on active duty, or I am a reservist, how meaningful is this new curriculum to me? And is it really that visible a change? How will it help us win over the hundreds of thousands of active and reserve officers and enlisted sailors we already have out there? I realize it should be done, but I’m not sure that it characterizes a good short-term win.”
That comment started us thinking, and from there, we more clearly defined characteristics of our short-term wins. In order to gain support out in the field, we needed successes that on the one hand were visible and on the other meaningful. This would make the wins really hit home. So we literally looked at everything we might do. Then we pinpointed which activities met our criteria and tried to create a timeline that would produce a continuous stream of successes.
For example: If we were to be one force, we needed to do a much better job of matching the skills among reserve personnel with the continually growing needs of the active Navy. Until recently, this was a long, tedious, manpower-intensive process. It didn’t always produce the desired results within the required time frames. Finding a readily available reservist with public affairs skills and Korean language proficiency, or an information technology specialist with expertise in information security, often meant relying on word of mouth. You can imagine what a difficult task that is in two very large and distinct organizations.
We decided we could record our Naval Reservists’ civilian and military skills into a useful, interactive, flexible, Web-based database. Authorized Navy personnel could quickly search for certain types of skills. There would be some individual privacy requirements, but we thought we could address these issues. Here was a project that would be meaningful to many people. It would be visible to many people. And it would be inexpensive and easily implemented because we could adapt architecture that was developed, funded, and already in use by another Defense Department agency.
Reservists, using password protection, can now directly post and update their education and civilian skills, including language and equipment proficiencies, and personal contact information. Authorized active Navy personnel can tap into the Web site and describe their request. They view online reports describing the skills, experience, and qualifications of persons who fit the profile, but not names and contact information. Active Navy personnel can then e-mail our Naval Reserve Command in New Orleans, which will act as intermediary for matching up the requirement with the available reservist. The system isn’t perfect, but it is visible to many people and is seen as useful to many.
Our successes are helping people in both forces believe in what we are trying to accomplish. In a little over thirty days, I received messages from the active Navy admirals in charge of the Pacific Fleet, Mediterranean and North Atlantic areas, and the Naval Air Forces in the Mediterranean. Their messages were uniformly positive. Bit by bit, we are showing our officers and enlisted sailors that we are serious about having One Navy. We’re showing them that the vision of a One Navy Force is working and that it is not just talk.
If you have been a part of enough successful change efforts, you will understand the power of visible, meaningful, and unambiguous wins. If you have not, you can miss the mark. Too often we create wins that we see, but which others do not, at least not to the same degree. Visiting an office in Japan, we see a breakthrough in a cancer drug using a new method of drug development. We find the victory and are able to ask questions and poke around. We conclude it is a big win and we leave pumped. Our colleagues in New Jersey read about the experiment and are excited, but not nearly as much without actually seeing the animals, talking to the researchers, and feeling the energy in the office. Too often we create wins that are meaningful to us, but much less so to others. We have enormously strong feelings about cancer, and though the key research personnel in New Jersey share these feelings to a degree, their hearts are invested much more in the problem of antiseizure agents. So while we are deeply moved by the Japanese wins, many of our colleagues in New Jersey are not. “Oh yes,” they say in a very rational manner, “this is important.” But they don’t rush to understand the development process that created the breakthrough. They don’t change their behavior. And that’s a problem.
In “New Navy,” a group very deliberately tried to avoid this problem by (1) clarifying the criteria for a good short-term win and (2) selecting projects based on that criteria. The educational program could have been helpful, but not as much as a resource-finding system that was highly visible and that was generally more valued than education. The results of a curriculum change could have been evaluated, but the Web site provided much more measurable outcomes.
Choosing What to Target First
The order of projects can also make an important difference in large-scale change efforts. You can choose what to target first based on a logic that seems eminently rational but which does not supply enough wins fast enough to build necessary momentum. Suppose the vision is globalization. One choice that seems rational is to work on the manufacturing piece before the marketing. Make it before you sell it. Focus first on building a plant in Frankfurt. But building the Frankfurt factory might easily take two years, a hundred million dollars, and then another year to assess whether the firm can handle its first German manufacturing facility. During this time, unambiguous, visible, meaningful wins would be hard to find. A less obvious but better choice is, in a sense, to sell a product, then make it. Put together a marketing plan for Germany. Implement the plan at minimum cost with a product from Chicago. Achieve a first clear success in less than a year.
In choosing well what to target first, you must satisfy the most basic criteria: achieving visible, meaningful, and unambiguous progress quickly. Beyond that, relatively easy options are obviously attractive—it is cheap and fast to open a Frankfurt office versus expensive and slow to build a plant. The easiest of the easy are often called “low-hanging fruit.” Less obvious to many people, but also important, are possibilities that focus on a powerful person or group whose help you need.
The Senator Owned a Trucking Company
From Ron Bingham
One of our state senators owns a trucking company. He’s an important person whose support could make a difference to our change effort. I thought, to help us start building momentum, what can we do for trucking companies?
I went to talk to him and it turns out that he is really mad that the state makes him fill out fifteen forms a year, some of them very long. “Do you know how much time and effort this takes?” He has his secretary dig around and find the forms. “Look at this!” he says. He doesn’t quite wave things in my face, but that’s the idea.
I look at the forms and my first impression is that this is bureaucracy at its worst. “The same information is asked here and here and here.” He says it politely, but I think he would like to strangle someone. “When I fill out some of these, I have to get three or four people involved.” I can easily imagine that. “We want to run a company that has jobs and customers. We don’t want to fill out unnecessary forms.”
I went and met with our change team in the transportation department. They had been struggling a bit to get cooperation with a lot of senior people in the department. You see, in government—at least in old government—there was often a “I’ll wait you out” kind of approach. Basically, if you stall long enough, the governor will change and the program that has been irritating you will go away. Well, the transportation group had been running into this, so they were ready for suggestions. I met with them and told them what the senator had told me. I said, “You guys need to put fixing these forms on the top of your agenda.” They didn’t agree right away. They basically said, “Jeez, Ron, we’ve got all these great and big things we need to get completed here and you’re trying to sell us on changing a few forms. That hardly seems like the grand change vision we had pictured.” I understood where they were coming from. They had all this energy. They wanted to change the world. But they weren’t getting anywhere because key constituents like the senator weren’t helping them. I explained how getting this win for the senator, while taking time up front, would actually give them more credibility and support to do the things that were really important to them. So somewhat grudgingly they started down the path of re-designing the licensing process. It took maybe a month to get done. And they did an amazing job.
For all those who say “What can you do with government, it’s just inherently a mess,” they should listen to this. A vision of less bureaucracy, more efficiency, and better service to the public is not unrealistic. The transportation team reduced the paperwork from fifteen forms to one. And they didn’t lose any key information, didn’t undermine any needed government function. That’s the sort of change that is possible, the sort of change that so many people inside and outside the government didn’t think was possible. That’s the sort of change that if you thought it wasn’t feasible, you wouldn’t waste time and resources trying to help someone who did.
When we were done, I took this back to the senator and showed it to him. “Damn, you guys are really doing something,” he says. Before that he had heard briefings on our work, but it was all talk. Now he could see it. It wasn’t just talk about another change project. And he could feel it because it affected something that was important to him. After that, the senator was one of our biggest supporters.
We have had several of these short-term successes, and now people believe in us and our work. The resistance has gone down, and the successes have helped make it real for the team. They don’t have to wait three years to feel like they are making a difference.
In selecting where to focus first, a key criterion applied in “The Senator” was to assist a powerful person as soon as possible. The assistance can alter the person’s feelings about the change effort, which can increase his or her support of that effort. This behavior change can produce more subsequent wins than if a less powerful person were helped.
The application of this principle can lead to a very different starting point than a more linear, “logical” model. The application of this principle can seem less “efficient” than some other possibilities. But who needs a fuel-efficient car if the driver becomes bored, stops, and never arrives at the finish line?
And If We Can’t Produce . . .
In some cases, all sorts of factors can block us from producing powerful enough wins at a pace that is needed. How we deal with this reality can be very important. When the wins are not there, the temptation, the oh-so-great temptation, is to stretch the truth, to exaggerate a bit. Not to lie, of course—we’d never lie. We just put the best possible light on events. Right?
Hoopla
From Dave Pariseau
We have been working to introduce a new IT system and new ways of working across our major operating divisions. This has been one of the largest changes our company has undertaken and it’s been painful at times. Twenty-four months into the effort, it was not obvious to most people whether this was working. They felt pain but little gain. It was not at all clear to top management what the financial paybacks were. Those leading the change were under a lot of pressure to produce some tangible successes, some wins to show people who were suffering that we were on the right track.
The core project team started sending a weekly e-mail to everyone in the company called “Message of the Week.” It was a status update. I can remember one that said “90 percent of our pre-go-live objectives have been met. Nearly all of our people have been trained and they are prepared and ready to do their jobs.” Well, there were a lot of employees who just didn’t agree with that message. The people who would be using the new system, who might have been trained on how to use the new software, were nearly all saying they had no real idea about how their jobs would change when the machine was switched on. Many of the project teams who were based on each site, and who were much closer to the way the business worked than the core project team, totally disagreed that 90 percent of the work was done.
Every communication we received was pretty much the same. As time went on, if anything, it got worse. Message of the Week seemed to have turned into project propaganda. One message said that a division had been making great strides with the new system and work processes, that they had improved their efficiency by something like an incredible 500 percent. It would make you think we had won World War III! But I remember some of the people from my division who were in regular contact with those in the “500 percent improvement division.” Our people said they only heard complaining.
It was like this everywhere. People were finding it really hard to adjust to the new software. They would read these communications and be thinking, “This is a nightmare. We haven’t won World War III; we’re going down! What are they talking about?”
It got so bad that even when Message of the Week told of real successes, things that we really had achieved as a result of all of the effort, the credibility of the communication had become so low that people ignored the message. I’m trying to remember a “good” piece of news that I actually believed in, and I can’t! This is despite the fact that I have been committed for the past three years to seeing the change effort be successful.
Part of this may be our culture. We seem to be more comfortable communicating “sunshine and roses.” You know: “Be honest, but positive whenever you send a message like this out.” But more than that, when the good results just didn’t happen, we started to feel a bit desperate in the face of some criticism. So we overplayed the positives to such an extent that they became unbelievable, regardless of whether they were real or imagined. So the skepticism grew, and this was really bad.
I suspect that any form of hoopla is a mistake.
An Exercise That Might Help
Make a list of projects or tasks that could be tackled by empowered people within the organization in which you have influence—projects or tasks that could be short-term wins.
1. For each item on the list, assess the following:
• When could you realistically get this done? How many months?
• How much effort and expense will it take? Grade it on a 1 to 10 scale, from almost no effort to huge time and expense.
• How unambiguous will the win be? Try another 1 to 10 scale.
• How visible will it be? (1 to 10)
• Will this be viewed as a meaningful win? (1 to 10)
• Who will see it as meaningful? How powerful are these people?
2. Given these assessments, which of the items on your list should receive priority?
• Pick the top five.
• What’s number one?
From this account, we don’t know exactly why they had no short-term wins. Perhaps they didn’t pay sufficient attention to the issue. Perhaps the early steps in the change process were not done well, making the wins task much more difficult. Whatever the case, they found themselves in a box and then did what is so tempting—stretching the truth. Possibly they were stretching the truth in their own minds, and not in any sense lying. Possibly they did not understand clearly that wins must be unambiguous. The result was disastrous. When their credibility collapsed, even a legitimate win was viewed with suspicion.
The best solution to the “Hoopla” problem is to never get into a position where it seems necessary to stretch the truth. The better you understand the issues in this chapter, in the entire book, the better the odds that you won’t. The second-best solution is never to try to exaggerate your way out of the box. Honesty always trumps propaganda. And honesty starts with being truthful with ourselves.
Being honest with yourself isn’t a bad strategy for all the steps in large-scale change.
Step 6
Create Short-Term Wins
Produce sufficient short-term wins, sufficiently fast, to energize the change helpers, enlighten the pessimists, defuse the cynics, and build momentum for the effort.
What Works
• Early wins that come fast
• Wins that are as visible as possible to as many people as possible
• Wins that penetrate emotional defenses by being unambiguous
• Wins that are meaningful to others—the more deeply meaningful the better
• Early wins that speak to powerful players whose support you need and do not yet have
• Wins that can be achieved cheaply and easily, even if they seem small compared with the grand vision
What Does Not Work
• Launching fifty projects all at once
• Providing the first win too slowly
• Stretching the truth
Stories to Remember
• The List on the Bulletin Boards
• Creating the New Navy
• The Senator Owned a Trucking Company
• Hoopla
Step 7
Don’t Let Up
After the first set of short-term wins, a change effort will have direction and momentum. In successful situations, people build on this momentum to make a vision a reality by keeping urgency up and a feeling of false pride down; by eliminating unnecessary, exhausting, and demoralizing work; and by not declaring victory prematurely.
Keeping Urgency Up
The most common problem at this stage in change efforts is sagging urgency. Success becomes an albatross. “We’ve won,” people say, and you have problems reminiscent of those in step 1.
PE Ratios
From Leonard Schaeffer
When we began, nearly everyone in the company was motivated to change because of the threat of being closed down. Then, as we started to turn ourselves around, there was a lot of excitement throughout the organization. People were motivated by our recent success and challenged by the new challenges. As we made more and more changes, we kept the momentum from slowing by comparing ourselves to similar healthcare companies. We explored our strengths and weaknesses along a number of dimensions in each of our business divisions. On top of that, I was out there talking face to face with all the people in our organization once a month. I would try to explain why we were making the changes and talk about the metrics that we were trying to achieve and the competitors we faced. There was Q&A. As we grew larger, we used teleconferencing once a month to get the same messages out.
When we started to lead the field, comparing ourselves to our competitors became a piece of cake. If anything, we kept reconfirming the fact that we were miles ahead of everyone. In light of this success, we were faced with the tendency to fall into complacency. After all, things were good; we were at the top of the mountain. What was the reason to keep on renewing ourselves, to keep on building the stronger organization that would inevitably be needed in the future? People began to say, “But we are number one.” Even worse for me, “Why won’t the boss just let up?”
This was no good. But what could I do?
Now we’ve started using the idea of looking at ourselves “from the investor’s point of view.” What that means is that we’ve started to compare where we are in relation to other investment opportunities within the broad healthcare field. The real message now is: We’re in competition not just with firms like us but also for investor’s dollars. This is no longer about just us and how well we run our business. This is no longer just about our success in relation to the competition out there creating the exact same products and services as we do. This is about recognizing the fact that other people are out there in the healthcare industry doing some pretty amazing things. Those people are getting a lot of attention and a lot of money from investors. So we may be the best at what we do, but if another company can create a price to earnings [PE] ratio of 50 and our PE is 12, boy, we’ve got trouble.
The reaction to this new focus has been very interesting. With some effort at helping people understand this idea, a lot of them got a renewed sense of urgency pretty quickly. They started to see the loss of potential investors as a threat and they started thinking about ways we can improve our own position. They began recognizing that there are a lot of newer companies who are beginning to offer some of the same services we do.
There are some people, however, who still say, “Company X is in the business of doing Net-based software, so it’s not a good comparison. People are investing in those companies for different reasons. They’re attracted to the technology, or to the newness of the company. We can’t compare ourselves to them.” Maybe it’s just human to want to think this way: They aren’t relevant, so we’re fine. I’ve been learning that you can never overcommunicate in helping people deal with these sorts of things. You have to be there talking with them as much as possible.
To keep you moving, in many situations it’s going to be essential to have an external problem. If you are just going to beat up on people and say we have to do better, it doesn’t work. People don’t really believe you and it’s not at all productive. Making more money doesn’t do it either. There has to be something real that they can see outside that leads them to say “We haven’t made ourselves into the organization we should be. We need to do more. We need to try harder. I’m willing to try harder.”
It’s easy for those driving change to allow urgency in the organization to drop when short-term performance rises. It’s easy then to become frustrated and to “beat up” on your people. It’s easy to declare victory too soon and become complacent yourself. This happens all the time. These traps are inherent in the very nature of large-scale change.
In “PE Ratios,” Schaeffer tried to deal with the urgency problem by shifting people’s frame of reference, how they looked at the situation. He used a new external comparison. How well such an approach works depends mostly on whether it changes how people feel about what they see. When they are tired, an intellectualized discussion of statistics can be twisted to fit complacent thinking. “Well yes, but what about . . . ?” Their reaction can be very different if they see a boss, in face-to-face communication, show his sincere belief in the new frame and show urgency based on that belief. Their reaction can be different if anyone else with credibility does the same—mutual fund managers, customers, and so on.
Almost all the step 1 methods can, with appropriate modifications, be used here. Imagine a firm having produced wave after wave of change, having its bottom line explode upward, having most employees and managers saying “You can’t do better than this,” and yet having many areas where the transformation has not even started—areas like purchasing. Then this guy has a college student do a little study about how many different kinds of gloves the firm buys. . . .
It’s easy for those driving change to allow urgency in the organization to drop when short-term performance rises. It’s easy then to become frustrated and to “beat up” on your people. It’s easy to declare victory too soon and become complacent yourself. This happens all the time. These traps are inherent in the very nature of large-scale change.
In “PE Ratios,” Schaeffer tried to deal with the urgency problem by shifting people’s frame of reference, how they looked at the situation. He used a new external comparison. How well such an approach works depends mostly on whether it changes how people feel about what they see. When they are tired, an intellectualized discussion of statistics can be twisted to fit complacent thinking. “Well yes, but what about . . . ?” Their reaction can be very different if they see a boss, in face-to-face communication, show his sincere belief in the new frame and show urgency based on that belief. Their reaction can be different if anyone else with credibility does the same—mutual fund managers, customers, and so on.
Almost all the step 1 methods can, with appropriate modifications, be used here. Imagine a firm having produced wave after wave of change, having its bottom line explode upward, having most employees and managers saying “You can’t do better than this,” and yet having many areas where the transformation has not even started—areas like purchasing. Then this guy has a college student do a little study about how many different kinds of gloves the firm buys. . . .
This is where our “Action Labs” come into play. Action Labs are cross-company project teams that are given an unusual amount of leeway and power. Members of an Action Lab work full-time for a few months. So it’s very intense. They have the right to talk to anybody they want, do anything they want, and operate with very few boundaries. They typically bond and listen more carefully to each other. So the person from one part of the organization starts to understand another part for the first time. They also become very candid with one another. As a group, they become more daring than any individual. With our encouragement, they start pursuing problems, start looking for solutions, in a way that just wouldn’t normally happen on the job. We give them permission to be very creative and bold. Not all do so, but in some cases it’s marvelous.
Our last lab was set up to focus squarely on the investment planning problem. Eight people were taken off their jobs and put on this full time for six weeks. They talked to the CEO and the executive group, the heads of some of our business divisions, those people who reported to them, the people who planned the budgets and did all the analysis, even the employees who type up the numbers and who have to keep adjusting the figures.
One thing the investment planning team did was to make a video that made fun of how people behaved when they put a budget together. It was a lighthearted way of getting a very serious message across. The video was a skit with characters like the Merchant of Fear, the Glory Hunter, and the People Protector. All were over-the-top spoofs of the types of behaviors that existed. Like all good spoofs, they hit the issues dead-on.
The Merchant of Fear would increase his own budget by drawing out and working off of people’s fears. He would say things like “We had better keep a bit of reserve in my budget—just in case.” If you ever tried to tackle a Merchant of Fear, he would have at least ten good reasons why he needed that amount of money to avoid having the company’s network explode and kill one billion people, maybe more. “We need to budget for these five things. Actually, now I think about it, we’d also better add these two extra things too because what would happen if it were a building that went up? In fact, while we’re at it, we might as well add these other thirty eventualities just in case we blow up an entire town.” And it wouldn’t matter that two of the budgeted items would have been enough. He would always have an answer as to why he needed more.
The Glory Hunter chased the high-profile management initiatives that could bring him fame and fortune. He focused on whatever was sexy at the time. He’d go after an important consulting project that had just been started or a key task force led by the CEO. He’d love a major engineering project where he could introduce new technology that would guarantee him a place in the company’s historical archives or his picture on the wall. He would not share credit or do what was necessarily in the best interests of the company. He would just demand budgets for what made him look good.
The People Protector didn’t want glory and wouldn’t necessarily pander to fears. His sole objective was to make sure that there were enough projects for his staff. If these could match their skill sets and happen near their home base, then all the better. Regardless of what work was actually needed, the People Protector would just calculate how many projects would be required for his 200 people over eight months and then set his budget accordingly.
The Action Lab team showed the video of these characters to the top twenty or thirty executives, the very people who were being spoofed in the film. You can imagine the reaction! There was total shock. Immediately everyone was trying to guess who the characters had been based on in real life. Somebody even asked, “Is that meant to be me?” Something like this would never have been done in the past, never been remotely considered. Yet with the labs and the support from the CEO, it happened.
I think top management burned the film. But it worked. They still occasionally refer back to the characters. “Watch out, this is beginning to look like Merchant-of-Fear talk.” It helped stop the old investment planning game in its tracks by exposing the types of behavior that went against the new, more shareholder-oriented vision.
We have found that not everyone works well in an Action Lab environment. You need people who are willing. You can’t coerce people into doing something like this. They also have to have the technical knowledge or base of experience to work on the problem. They need to be willing to challenge the status quo for good reasons, to ask “why,” and to question the rules instead of just accepting that something is set in stone because it’s always been done that way. And they need to be able to leave their desk with the agreement that they won’t be back until the lab is over. This last point is a real challenge. The types of people we need in Action Labs are typically not those who are easy to free up.
We have done ten of these labs. Not all have been great. The ones that have not worked so well did not have a clear focus or objective at the start. We’ve found if the groups do not work well because of the people dynamics, you have to make a decision there and then if it’s salvageable or not and go with it. But most labs have been very useful, and their actions have made a difference.
One of our biggest regrets with the last lab is that we didn’t find a way to make a copy of that video before it was burned!
Somewhere in the waves of change, you will have to attack the sturdy silos and difficult politics or you won’t create a twenty-first-century organization. In the early stages of a transformation, the silos and politics can be too tough to handle. But eventually, you must choose to deal with this heavy lifting or you will never fulfill the vision.
In “The Merchant,” the company made progress not because of task forces per se. They made progress because they set up conditions that gave a group sufficient power to blast through the barriers and complete another needed wave of change. Oddly, the group was a task force—oddly, because we don’t think of task forces as powerful. But look at how they did it. First, the Action Labs groups were given great leeway. These sorts of cross-organization task forces often fail because they are put on short leashes. Second, the members were given sufficient time. Typically, people on these types of task forces are supposed to do the work in addition to their regular jobs. Third, they were given the opportunity to gather a broad range of data. There was no “Well, yes, but the chairman is out those three weeks.” Fourth, they were not handed a conservative charter. There was no “Don’t stir the waters too much; be practical; make sure any ideas can be implemented,” the latter often a code phrase meaning “Make sure the ideas are so trivial that no one will try to block them.” Because there were none of these constraints, it helped give people, after easier waves of change were completed, the power to attack the particularly difficult challenges.
Also key in the success of the “Merchant” task force was its creativity. Write a play showing the problems. Hire actors and film it. Make it funny—to diffuse some of the defensiveness and to reduce the frontal attack on a norm of underlings not criticizing the bosses, perhaps even a norm of no heavy conflict allowed in public. If the fun came across as angry and ridiculing, the risk would have been much higher. But it didn’t. If the problems spoofed were not the spot-on real problems, a defensive person could trash the film. But apparently the task force did a good job of putting its finger right on the issues. If no one on the executive committee was frustrated by the destructive behavior, the top management could still have found a way to rationalize the “stupid” film and ignore it. But that was not the case here, and probably never is. The film gave those who were frustrated, a group that is often larger than is apparent, a legitimate tool, and a feeling of optimism, to try to eliminate unhealthy behavior. In combination with other actions—and other actions would have been necessary—the wall started to fall, and the change process had a chance of making it all the way to the end.
Images can be powerful. Even if viewed only once, they can stick in the mind for a long time. A month later, someone could refer to “The Merchant of Fear” video and the idea (and feeling) would still be there because a strong image was instilled. That seems to be the way the mind works.
Not Killing Ourselves
Deep into a transformation, even if urgency remains high, even if people want to take on the big problems, and even if they succeed in generating waves of change, they can still fail because of exhaustion. They find they have to keep the organization running, which means doing all the old work. On top of that they have to handle additional work to create the future. So people are overwhelmed and eventually start to resent it. For many individuals, the situation can feel as if there is no solution—which isn’t true.
In successful transformations the answer is, at one level, very simple: When you have too much work, jettison some.
Reducing Twenty-Five Pages to Two
From Ken Moran and Rick Browning
After the teams had been functioning for a while, and the change process seemed to be working, we began getting a ton of feedback about how we were creating too much pressure on people in terms of workload. They were taking their day-to-day work home on the weekends. “Ken, my wife is complaining.” “Ken, this is no good, we can’t keep this up.” “Ken, if I call the local paper, send them to your office, then walk in and die, this will not help your career.”
An e-mail went out to people saying that this was not incremental work. This was not “Do your job and add all this new activity.” If you were on a working team, that was part of your job. If there was other work to be done, we needed to reallocate it further down the hierarchy or not do it at all. This was, and still is, the only solution to the problem.
When we look at all of our day-to-day activities and ask “Does this really add value? Do I absolutely need to do this?”, we often find many ways to save time. We did this with our monthly report. Every month, each department produced this huge report that got e-mailed to fifty to sixty people. It was at least twenty-five pages long. It highlighted everything, ranging from new product development goals to status updates on the various initiatives. Who knows how much work went into creating and reading the reports. But some of us stopped reading them. If we wanted to know whether or not we were leading the market in sales, we’d have an assistant run a report. If we wanted to know how the marketing launch of our new product line was going, we’d call the VP of marketing. This was the information we needed to know. Unfortunately, it was either buried in detail in that twenty-five-page report or not included at all.
Going forward, we’ve decided to change the monthly report. It will only be two pages long and it will highlight financial metrics that the department heads have agreed on (like sales, growth rate, budget). If a department has reached a major milestone, then it will be covered. However, individual project details by department have been eliminated. Think about it. Creating and then having fifty people read twenty-five often complicated pages versus creating and reading two pages.
If we can identify, recognize, and agree on what people can stop doing, then we won’t feel so overwhelmed. We have to focus on the important work or we’ll never create and adopt the new strategies. So what we need to do now, and what we are trying to put a framework around for the next three or four years, is to continue to identify things like the monthly report and replace them with activities that will move us forward.
For some, making the adjustment will be difficult. We all need to be doing more to help these people.
In “Twenty-Five Pages to Two,” one simple change makes a difference. One simple change eliminates what could add up in a year to a thousand hours of wasted managerial effort. The change visibly shows what the boss wants others to do. It is an action that makes his words on the subject more understandable and credible. And it is an action that has consequences that people feel.
The best way to handle the overwork problem is with conscious effort as early in the process as possible. You anticipate the issue rather than suddenly finding it explode in your face. Then you purge your calendar of everything that is a leftover from history and that has no current pressing relevance. You stop the unnecessary Tuesday morning meeting that has been a fixture for five decades. You eliminate the six different kinds of reports that land on your desk, that take time to understand, and that are no longer needed. You use teleconferencing to cut out travel. You no longer attend meetings where your presence is not essential. You kill pet projects that add little to the change effort and yet suck up time and money. You delegate more. You find what can and should be done by others and let them do it. You delegate not only down, but up and sideways. If peers can better do the work, you let them. If bosses can better do the work, you let them. Considerations of prestige—look at all the
important work I do—are put aside. Instead, you relentlessly push work off your desk that others can do, should do, and will do. You fight the egotistical tendency most of us have to think we must do something because others cannot.
People are not machines. We need more than maintenance. We need the rejuvenation that comes from sleep, relaxation, and fun off the job. Everyone engaged in a big effort to change a company, a department, or a work group should probably have a banner above the mirror in his or her bathroom at home, a banner to be seen every morning and night that says “Dying will not help.”
Our Favorite Step 7 Story
This is creative.
The Street
From Jack Jacobs
We had made substantial steps forward in terms of improving customer service, a key element of our new vision. We improved our percentage of on-time and complete shipments from 50 percent to 99 percent, even though 50 percent is pretty much standard in our industry. Our success not only helped our customers; it also helped demonstrate that we were on track. Unfortunately, although improving our delivery percentages so dramatically was a huge win for us, it also suddenly left us open to renewed complacency. The question was, What do we do next?
As it turned out, the changes we made to improve delivery time actually provided us an opportunity to further our vision and values and keep the change rolling. We had removed all our on-site inventory and shifted responsibility for it to our suppliers. The result was we had thousands of square feet in the manufacturing facility that had no use. You walked into our facility and it looked more like an empty warehouse than an assembly line. That’s how much space we opened up. We immediately started looking for new materials to store there. Given all the manufacturing we did throughout the southeast, we figured that shouldn’t be difficult. We began looking around for other raw materials to put in our new space, things like lumber, steel sheets, plastic rollers, steel pins, and so forth.
Then one of our designers approached me with a brainstorm. “Why don’t we use the space to expand the offices?” At the time, we had in the facility a few offices for plant management. But by and large, we housed managers at headquarters, which was about a five-minute drive away. This was not surprising given the plant was one of those boxy, windowless buildings that provided shelter from the elements but little else. We started to think about options for turning the space into offices for all our plant administrative staff and managers.
Given my preoccupation with making sure the change continued, I went back to our vision to see if redesigning the factory fit into the larger change program. What I found was the concept of community. We were committed to building community, believing that we would gain strength and competitive advantage by uniting the thousands of people that work for us. What I realized was that redesigning the manufacturing facility might provide an opportunity to address the whole notion of community. So I threw the question out to our design team. “How can we reconfigure the plant in a way that strengthens community and visibly continues our change program?” What they came up with was truly brilliant.
We decided that community could be strengthened if we found a way to increase the interaction between office workers and line workers. We wondered if we could somehow do this with the available space in the plant. As we thought about this, we got more and more ambitious. What started as a simple idea quickly morphed into a more complicated, awesome idea. We decided to shift the manufacturing line to the center of the factory and then wrap a broad corridor around it. The ceiling of the corridor would be covered with glass so that even on the most cloudy winter days there is light flooding in. On the other side of the corridor we would wrap our administrative offices. So basically the factory would be in the middle, the offices on the outside, and in between we’d have this broad corridor.
Next we decided to put all the common-use rooms like washrooms, coffee rooms, etc., off of the main corridor so that they would be shared by both office workers and factory workers. For factory workers to use the shared washrooms, they would have to come out of the factory and walk along the corridor. The same is true for the office people. As a result both groups not only share the same facilities but also share the corridor. So there would be constant intermingling. Everyone in the facility would need to use this corridor to get to his or her respective areas.
In fact, the corridor became so well traveled that it was dubbed The Street. The Street is superbly conducive to the mingling of the factory and the office employees. In the coffee room, the restroom, the meeting room, it brings us together. It provides a chance for us to let our hair down. If that doesn’t build community, I don’t know what does.
So we’ve managed to not only make more efficient use of the space provided from our first change, we’ve been able to use that space to build community and ultimately reinforce and continue our change efforts, and to do so in a very visible way. Nobody could miss this. To some degree we were lucky. But the key was a team of people that saw that this is what we should focus on. And we did.
Think of all the ways the people in “The Street” could have pursued the collaboration theme. The most obvious would have been a new program. There might have been speeches, workshops, perhaps a change on the performance appraisal form. All this could have helped, but it would have encountered a workforce tired of change and an employee base whose sense of urgency had sunk. Under those conditions, people often throw up their hands, convince themselves that enough of the vision is complete, declare victory, and resist new programs, no matter how well designed.
The change effort in “The Street” succeeds not because it directly creates collaboration or new collaboration norms. It works because everyone sees the company building a space, at some cost, that makes it much easier for employees of all sorts to interact, work together, and be together. This gives huge credence to vague, lofty, visionary ideas like “We should collaborate more.” The Street works because the blue collar and office employees see each other often enough for mutual negative stereotyping to decrease. “My goodness, he’s human too, wears clothes, speaks English, doesn’t eat children for lunch.” A decrease in negative stereotyping increases the chances of collaboration. So the achievement of the vision moves along. Another wave of change passes. The company moves nearer to the end of the process. And the firm has an innovative, twenty-first-century, the-PR-guys-are-going-to-love-it work space.
Step 7
Don’t Let Up
Continue with wave after wave of change, not stopping until the vision is a reality, despite seemingly intractable problems.
What Helps
• Aggressively ridding yourself of work that wears you down—tasks that were relevant in the past but not now, tasks that can be delegated
• Looking constantly for ways to keep urgency up
• Using new situations opportunistically (as in “The Street”) to launch the next wave of change
• As always—show’em, show’em, show’em
What Does Not Help
• Developing a rigid four-year plan (be more opportunistic)
• Convincing yourself that you’re done when you aren’t
• Convincing yourself that you can get the job done without confronting some of the more embedded bureaucratic and political behaviors
• Working so hard you physically and emotionally collapse (or sacrifice your off-the-job life)
Stories to Remember
• PE Ratios
• The Merchant of Fear
• Reducing Twenty-Five Pages to Two
• The Street
Video: Welcome to Week 7https://www.youtube.com/watch?v=_FzgNraZLGU&feature=youtu.be



